
The IAM page is inside the security section of AWS console

By default the root account has enabled acces keys, it is recomended to delete it, and use IAM user keys to improve security.
Also it is recomended to enable MFA (multi factor authentication).
Best practice recomends to use the least privilege access approach.
It is under account settings inside the access management menu.
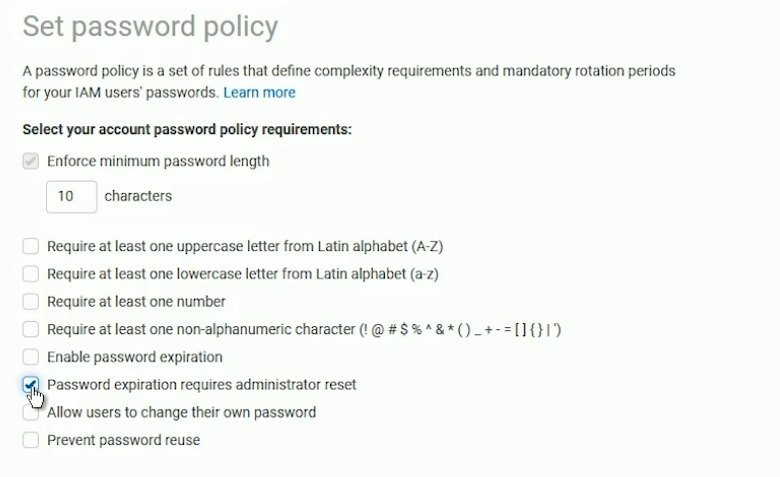
A password policy is a set of rules that define the data that forms the password an IAM user can set.
example 14 characters length.
You can single sign-on to a directory service (Open LDAP or Active Directory).
Principle of Least privilege access, for elevated or escalated access you need to add the user to other group.
So you create grous like:
Groups can be based on departments, organizational units, or programs, or dev lifecycle.
A Group can have until 10 policies attached.
A Policy is as set of permissions.
You add users to group to inherit the permissions assigned to the group.
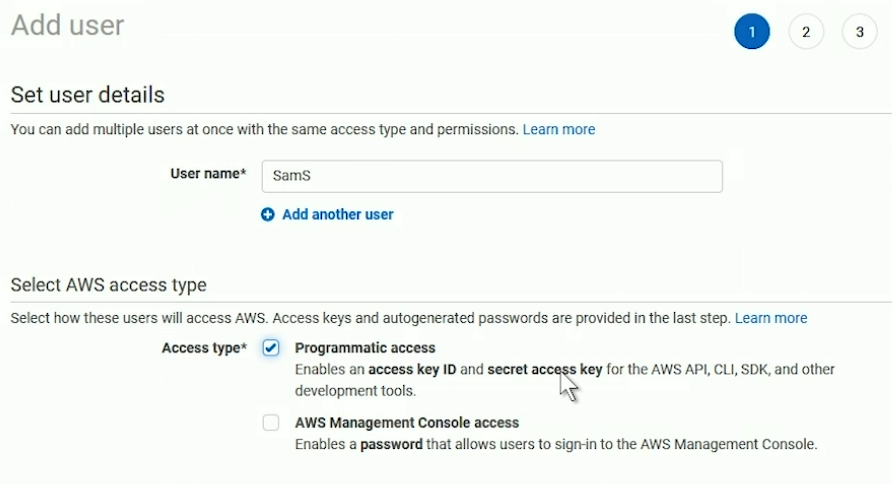
When you create a user you can:
A highest level policy: AdministratorAccess, at the Policy Summary you can see the list of services and the acces level for each one.
Policies can be applied to Users, Groups or Roles.
You can only apply 10 policies to an entity.
Deny takes precedence over allow permissions.
You can use the Policy Simulator HERE
The Access Analyzer use AI to analyze your resources access.
A role is an identity than has a permission assigned to it.
Intended to be assumed by a user, application or service.
A role does not have long-term credentials (passwords or keys).
AWS offers temp credentials for the lifetime of a session through STS (Secure Token Service).
IAM roles are a secure way to grant permissions to entities that you trust like:
A bastion host is a system whose goal is to offer secure access to a private network from an external network like the Internet
Must be hardened to reduce the chances of exploit and penetration
AppStream 2 is a dynamic bastion service, spins up fresh instances, it automatically terminates instances, must have SSO (single sign-on) in place , and requires HTML5 desktop browser.
Requires Programmatic Access permission
Access Key ID, it is used to identify the identity making the API call.
Secret Access Key, it is used to sign API calls.
Can be intsalled on windows using the installer or from python with pip
pip install awscli
To setup access key in the CLI you can run
aws configure
Applications running outside AWS will need access keys (AWS CLI or SDKs)
SDK use digital signatures to protect the message integrity from tampering, requests are valid only for 15 minutes.
Signing prototol version 4 offers forward secrecy (the actual secret key is not used for the digital signing, but rather a derived key).
Using SAML 2.0 federation, you can have your own Identity provider (Active Directory, eDirectory or OpenLDAP).
Changing the application ID that the identity pool is linked to will prevent existing users to sign-in using Cognito.